System & Access Requirements
Architecture Overview
The following diagram illustrates key system, network and security requirements for running DMC.
System, Network and Security Requirements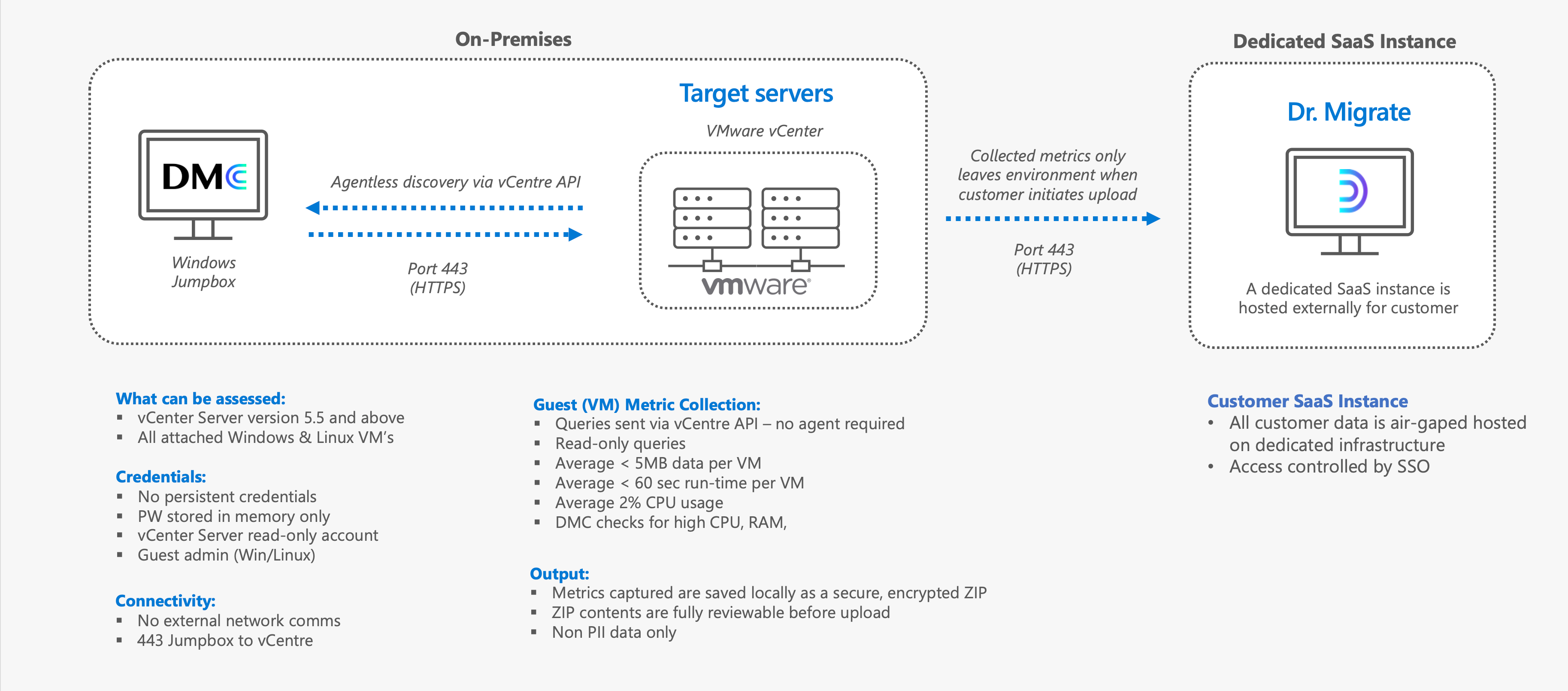
VMware Requirements
DMC is compatible with the following on-premises implemented versions and later.
| vSphere Version |
|---|
| vSphere 7.0 and above |
Server Requirements (ie Jump Box)
DMC can be executed from any Windows machine that has a network line of sight to the target vCentre and ESXi hosts. Typically, DMC is deployed from a designated jump box within the customer’s network. This system must adhere to the following specifications:
Hardware Requirements
| Component | Minimum Requirement |
|---|---|
| Operating System | Windows Server 2016 or later |
| CPU | 4 vCPUs |
| RAM | 8 GB |
| Storage | 25 GB free space per 4,000 VMs scanned (for temporary data storage). |
| Network | Line-of-sight access to vCenter and ESXi. (default port 443) |
Network Requirements
DMC requires network access to target vCenter(s) within the scope of discovery.
| Source | Destination | Ports | Purpose |
|---|---|---|---|
| Jump Box | vCenter Servers | 443 (HTTPS) | API communication for discovery |
| Jump Box | ESXi Hosts | 443 (HTTPS) | Transfer Guest VM discovered metrics |
Credential Requirements
Security Note:
- DMC is specifically designed to allow a customer Administrator to securely utilise their admin credentials for a one-time operation. This approach eliminates the necessity of creating a bespoke account, making it the recommended method for such tasks.
- All credentials are stored in memory only and never persist beyond execution.
- Credentials requirements are tailored for one-time use, allowing administrators to securely employ their personal credentials.
To ensure DMC can perform discovery the following permissions are required.
vCenter Access
| Account | Minimum Required Permissions | Reason |
|---|---|---|
| vCenter Admin Account | Read-only access to VMs, Hosts, and Datastores. Guest Operations execution role. Access to retrieve performance metrics |
Required to collect virtual infrastructure metadata, execute lightweight guest operations, and retrieve VM performance data without impacting environment stability. |
Guest OS Credentials
| OS | Credentials Needed | Permissions Required | Reason |
|---|---|---|---|
| Windows VMs | Domain Admin or Local Admin | Read system settings, software inventory, network stack, and processes. | Enables collection of system settings, software inventory, active processes, and network dependencies to assist with environment assessment. |
| Linux VMs | Root or Sudo-enabled user | Installed packages, active processes, and network connections. | Enables collection of system settings, software inventory, active processes, and network dependencies to assist with environment assessment. |
Least Privilege Setup
If a customer wishes to set up a Least Privilege account, the following roles must be configured.
Without vCentre Administrator account DMC cannot assess the health of the VMware environment. We recommend that a vSphere administrator checks the environment’s health before running DMC, as a safety precaution.
Customers can review VMware’s vSphere Health via:
🔗 View vCenter Server Health Status
Roles required for Least Privilege vCenter Permissions
| Role | Note |
|---|---|
| VirtualMachine.GuestOperations.Query | Allows DMC to query guest OS-level info such as file system and processes. |
| VirtualMachine.GuestOperations.Execute | Enables DMC to run lightweight commands inside the VM for inventory checks. |
| VirtualMachine.GuestOperations.Modify | Required for actions like copying files or scripts into the VM during discovery. |
| Read Only access to vCenter | Grants visibility into vSphere objects like VMs, hosts, clusters, and tags — essential for inventory mapping. |